1. The Centralized Intelligence Risk
Before AI adoption, sensitive enterprise data was naturally segmented across multiple systems, each with independent security perimeters. AI fundamentally changes this landscape by requiring data centralization for optimal performance.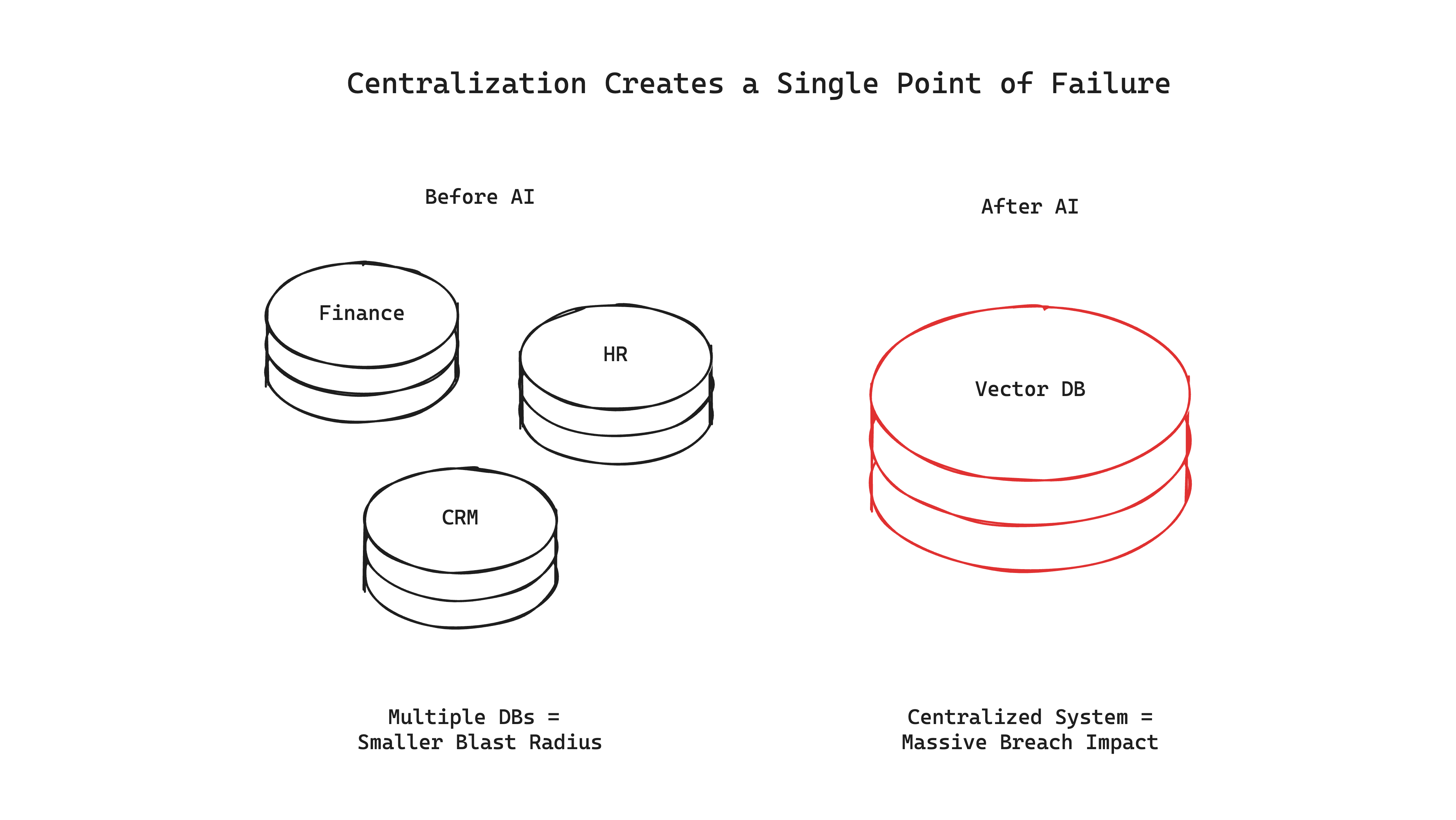
Vector Database Vulnerability Profile
Standard vector databases exacerbate this risk through fundamental design choices:Plaintext Storage
Embeddings stored without encryption, immediately exploitable upon access
Dense Information
Each vector encodes rich semantic content from source documents
ML-Optimized Format
Vector format specifically vulnerable to machine learning exploitation
2. Attack Mechanics
When attackers compromise a traditional vector database, they can execute a systematic intelligence extraction process: Attack timeline on standard vector DB:- Initial access (minutes): Exploit application vulnerabilities or cloud misconfigurations
- Data extraction (minutes): Download plaintext embeddings and metadata
- Inversion setup (hours): Deploy transformer models or gradient optimization
- Content recovery (hours to days): Reconstruct original documents with 80-99% fidelity
- Intelligence synthesis (days): Correlate recovered data across enterprise systems
Amplified Impact
Vector database breaches differ qualitatively from traditional data breaches:| Traditional DB Breach | Vector DB Breach | Impact Multiplier |
|---|---|---|
| Single application data | Multi-system intelligence | 10-100x |
| Structured data theft | Semantic relationship exposure | Qualitative difference |
| Point-in-time snapshot | Historical relationship mapping | Temporal amplification |
3. CyborgDB Security Architecture
CyborgDB disrupts the attack chain through a defense-in-depth approach that renders vector database breaches non-exploitable. This security is achieved through several key mechanisms:- In-use encryption: Embeddings remain encrypted even during computation
- Query unlinkability: Current searches cannot be correlated with historical patterns
- Insertion obfuscation: New data additions reveal no information about existing content
- Temporal isolation: Past compromises do not affect future security
- Customer key control: Encryption keys remain under customer management
- Zero-knowledge operation: CyborgDB operates without access to decryption keys
4. Security Guarantees
CyborgDB provides mathematically provable protections against the threat scenarios in the threat model.| Attack Vector | Standard Vector DB | CyborgDB Protection | Security Guarantee |
|---|---|---|---|
| Embedding extraction | ❌ Immediate plaintext access | ✅ AES-256-GCM encrypted storage | Computational security (2^256 operations) |
| Memory scraping | ❌ Plaintext in RAM | ✅ In-use encryption | Semantic security preservation |
| Inversion attacks | ❌ Direct ML exploitation | ✅ Ciphertext-only exposure | Information-theoretic privacy |
| Query correlation | ❌ Full access pattern visibility | ✅ Forward-private indexing | Unlinkability guarantee |
| Cross-system linking | ❌ Trivial metadata correlation | ✅ Per-record key isolation | Computational indistinguishability |
5. Getting Started
CyborgDB makes securing your AI database as straightforward as deploying it:Try CyborgDB
Get started in 5 minutes to evaluate security and performance

